About the user PIN and the certificate PIN
Starting with version 4.30, Redtrust introduces the user PIN as an additional security layer to help prevent unauthorized certificate use. The user PIN is unique to each user and can be applied to one or more certificates.
In contrast, the certificate PIN is tied to a specific certificate and may be shared by multiple users. Since version 4.32, existing certificate PINs can also be removed, giving administrators and users more flexibility and encouraging adoption of the user PIN instead.
Whenever possible, users should use their individual PIN to ensure better access control and reduce the risk of unauthorized use.
Where is it configured?
You can manage both PINs from:
-
The system policies.
This page explains how these two types of PINs interact. For step-by-step instructions, see How to set up and change the user PIN.
Interaction logic
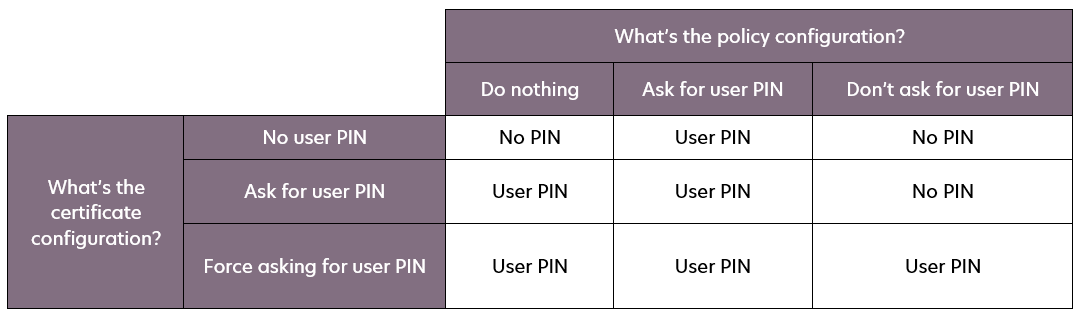
Certificates without certificate PIN
Certificates without a certificate PIN will follow this logic, depending on the user PIN configuration:
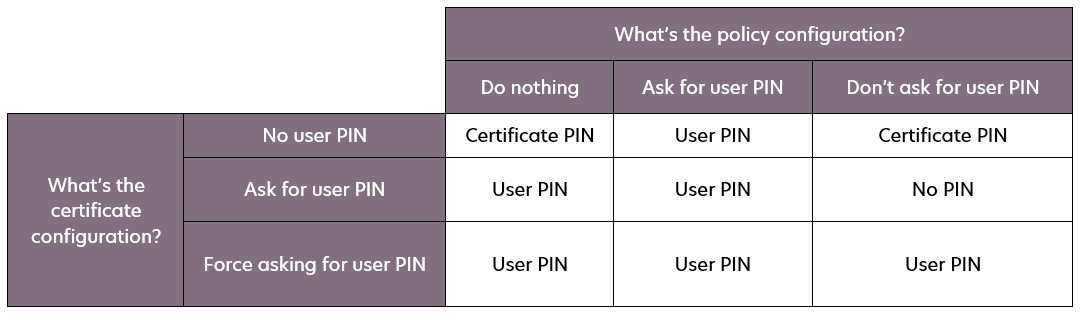
Certificates with certificate PIN
Certificates with a configured certificate PIN will follow this logic, depending on the user PIN configuration:
Special cases
Personal certificates
Personal certificates are digital certificates issued to an individual. Only the owner can upload and use these certificates. Policies cannot be used to grant access or delegate their use.
Since version 4.32, you can remove existing certificate PINs from older personal certificates. To do so, you must provide the current certificate PIN. This change is consistent with our recommendation to use the user PIN as the primary access control. Removing the certificate PIN helps ensure that only the certificate owner’s user PIN is required, simplifying management and improving security.
Uploading certificates
When a certificate is uploaded to the personal area, the logic may vary depending on whether a certificate PIN was defined at that time. If a certificate PIN was set during the upload, the system will accept either of the two PINs (user or certificate). This is designed to prevent lockouts or errors and to improve the user experience.
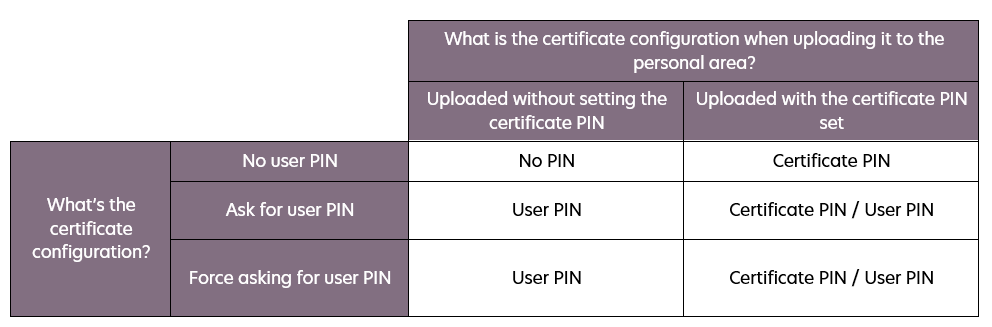
Summary
The way PINs are requested depends on the combination of policies, certificate settings, and how the certificate was uploaded. In most situations, the user PIN takes precedence, while the certificate PIN only applies if it is explicitly enforced at the certificate level. When a certificate PIN is defined during upload, either PIN can be used, which prevents lockouts and improves usability. Using the user PIN as the main method of access control provides stronger security and simplifies management across all certificates.
For information on how to configure the user PIN, see How to set up and change the user PIN.