Domains
Overview
In Redtrust, a domain defines the authentication method for a group of users to access the service. The available authentication methods depend on how users are configured to authenticate, as outlined in the table below. Multiple domains can be defined to accommodate multiple use cases. For example, a SAML domain could be created for an organization's users/groups from an IdP like Entra ID (formerly knows as Azure Active Directory) using the Windows Agent in attended mode, while a separate local users domain could be created to authenticate a Linux build server.
| Authentication source | Admin console | Windows agent (attended) | Windows agent (unattended) | Linux agent (attended) |
|---|---|---|---|---|
| Activation code | ✅ | ✅ | ||
| Entra ID | ✅* | ✅ | ||
| Certificate users | ✅ | ✅ | ||
| LDAP | ✅* | ✅ | ||
| Local users (Username/Password) | ✅ | ✅ | ✅ | ✅ |
| OAuth | ✅ | ✅ | ||
| SAML 2.0 | ✅ | ✅ |
* Users authenticate against the domain using their username and password.
General configuration options
You can access the domain creation wizard by navigating to Access > Domain and clicking on the New button. In the wizard you must define the domain's features.
| Option | Description |
|---|---|
| Alias | Defines what users will use to reference this domain when logging in to the service. For example, with a local users domain, a user with the username of John would login to the domain with an alias name of myDomain by entering John@myDomain. For SAML and OAuth domains the Alias can match the email domain of the users. For example, for an organization with emails formatted first.last@companyname.com, the alias could be companyname.com. |
| Type | Valid domain types include:
|
| Access to Personal Area | Defined whether the users of this domain can access their personal area. |
See UI screenshot
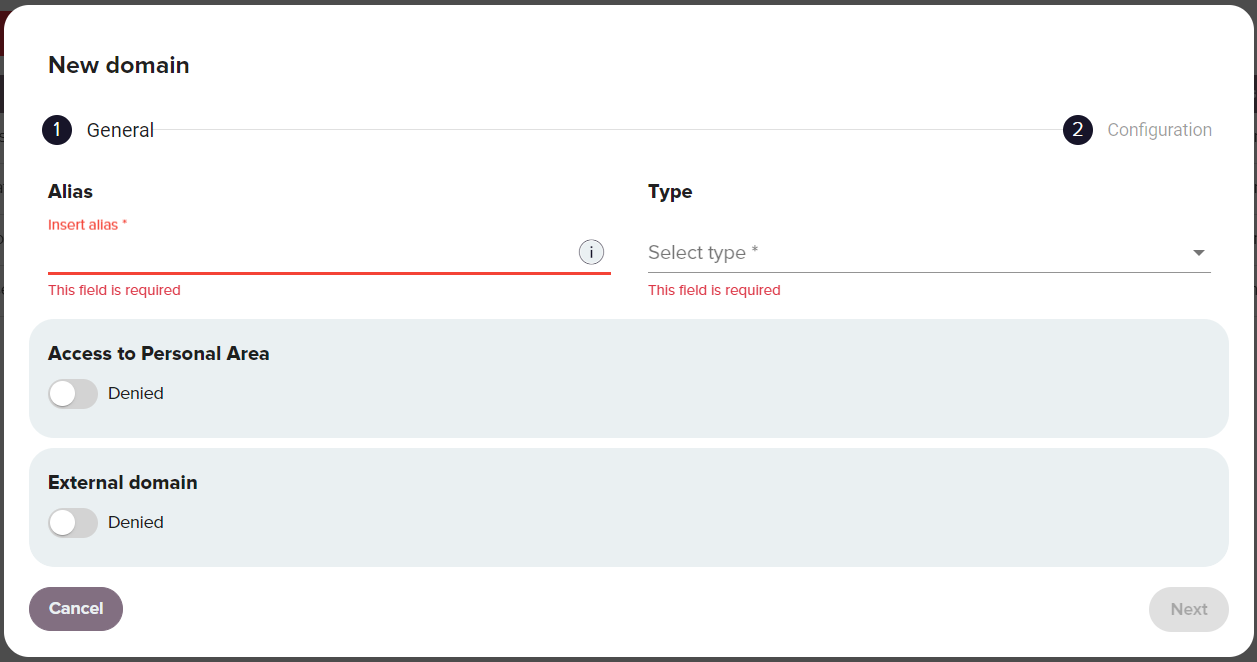
Other configuration options appear when selecting a domain type.
| Option | Description |
|---|---|
| Concurrency Per User | Setting for the domain to allow a single user to authenticate into multiple agent sessions simultaneously. This can be useful for short lived build pipelines and service accounts. |
| Limit Users | This field is optional. It's a limit on the number of users that a given domain can be configured with. |
| SSO Login | This button allows users to go directly to the Identity Provider (IdP). This feature applies to both SAML and OAuth 2.0 domains. If needed, multiple domains can be configured this way, enabling authentication with multiple IdPs directly from the login page. |
Entra ID and LDAP configuration
When choosing an Entra ID (formerly Active Directory) or LDAP type domain, new configuration options are immediately displayed in the window:
See UI screenshot
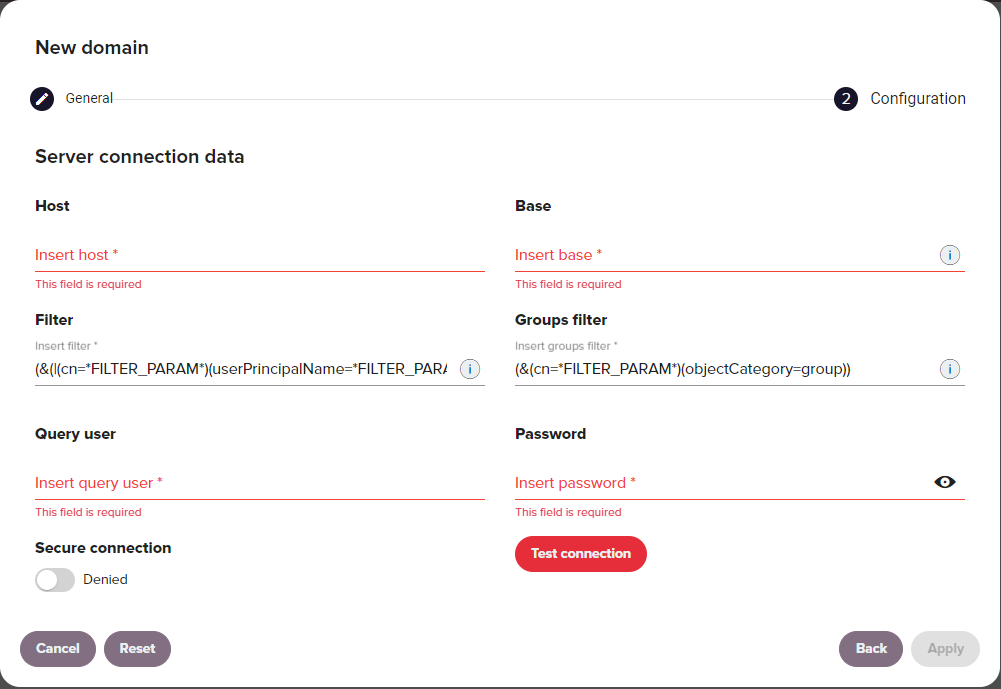
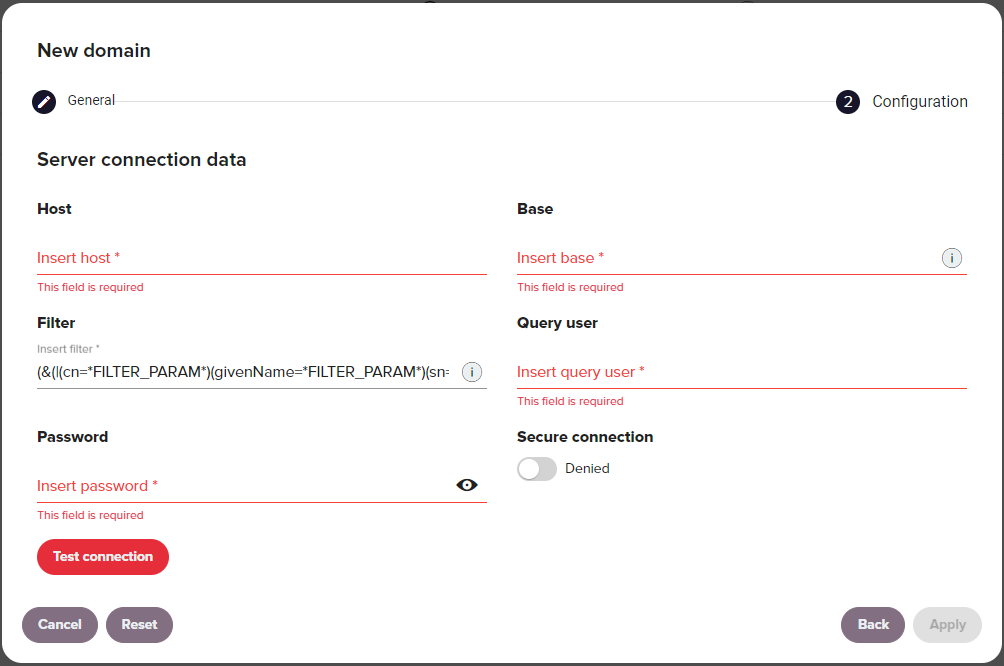
| Option | Description |
|---|---|
| Host | Defines the server address. |
| Base | Base DN from which the repository is visible to Redtrust. For example DC=Redtrust,DC=com. |
| Filter | Filter used for user searches in the directory. The string FILTER_PARAM represents the search term. A typical filter: (&(|(cn=*FILTER_PARAM*)(userPrincipalName=*FILTER_PARAM*)(sAMAccountName=*FILTER_PARAM*))(objectCategory=person)).Example: Searching for User1 replaces FILTER_PARAM with User1. |
| Groups filter | (Entra ID only) Filter used for group searches in the directory. The string FILTER_PARAM represents the search term. A typical filter: (&(cn=*FILTER_PARAM*)(objectCategory=group)). |
| Query user | User to connect to the external directory. |
| Password | Password for the query user. |
| Secure connection | Indicates whether the connection to the Entra ID server uses HTTP (not secure) or HTTPS (secure) protocol. |
Local users
See UI screenshot
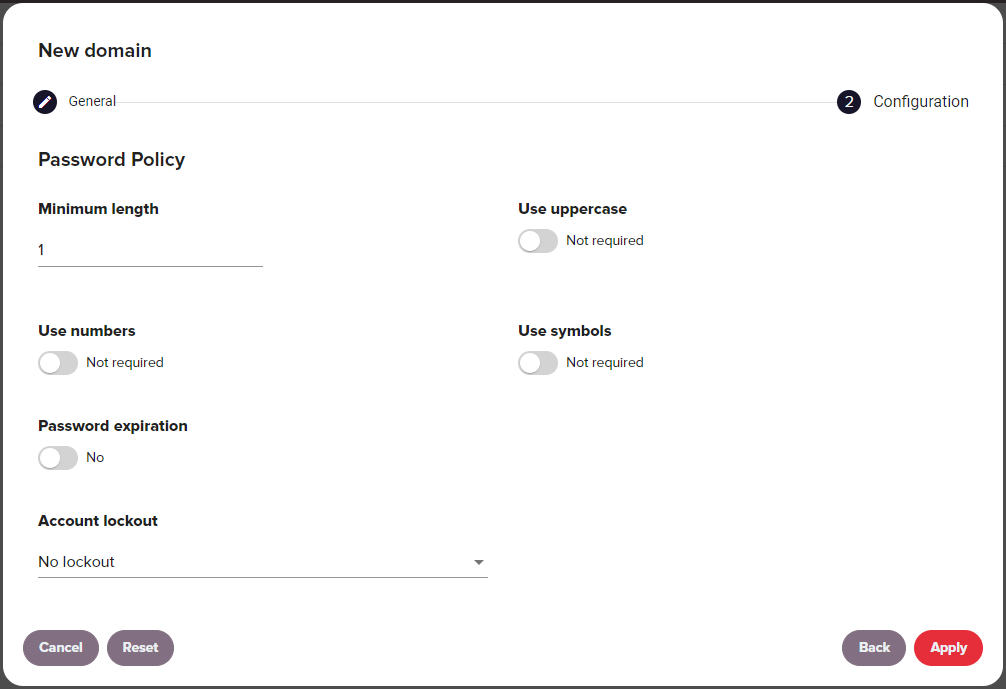
| Option | Description |
|---|---|
| Minimum length | The minimum required length of passwords. |
| Use uppercase | Require passwords to include uppercase characters. |
| Use numbers | Require passwords to include numeric characters. |
| Use symbols | Require passwords to include special characters. |
| Password expiration | This option sets a number of months before a password expires. |
| Account lockout |
|
OAuth
See UI screenshot
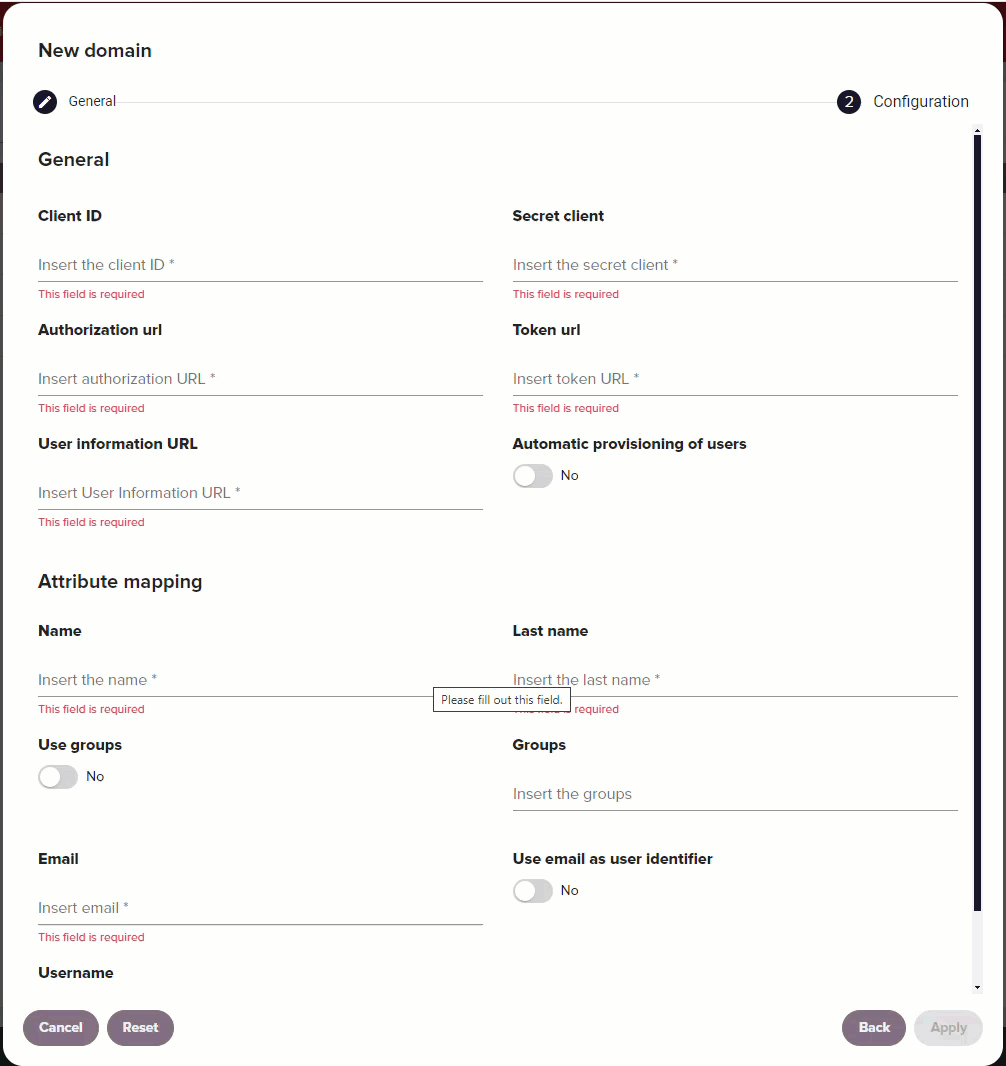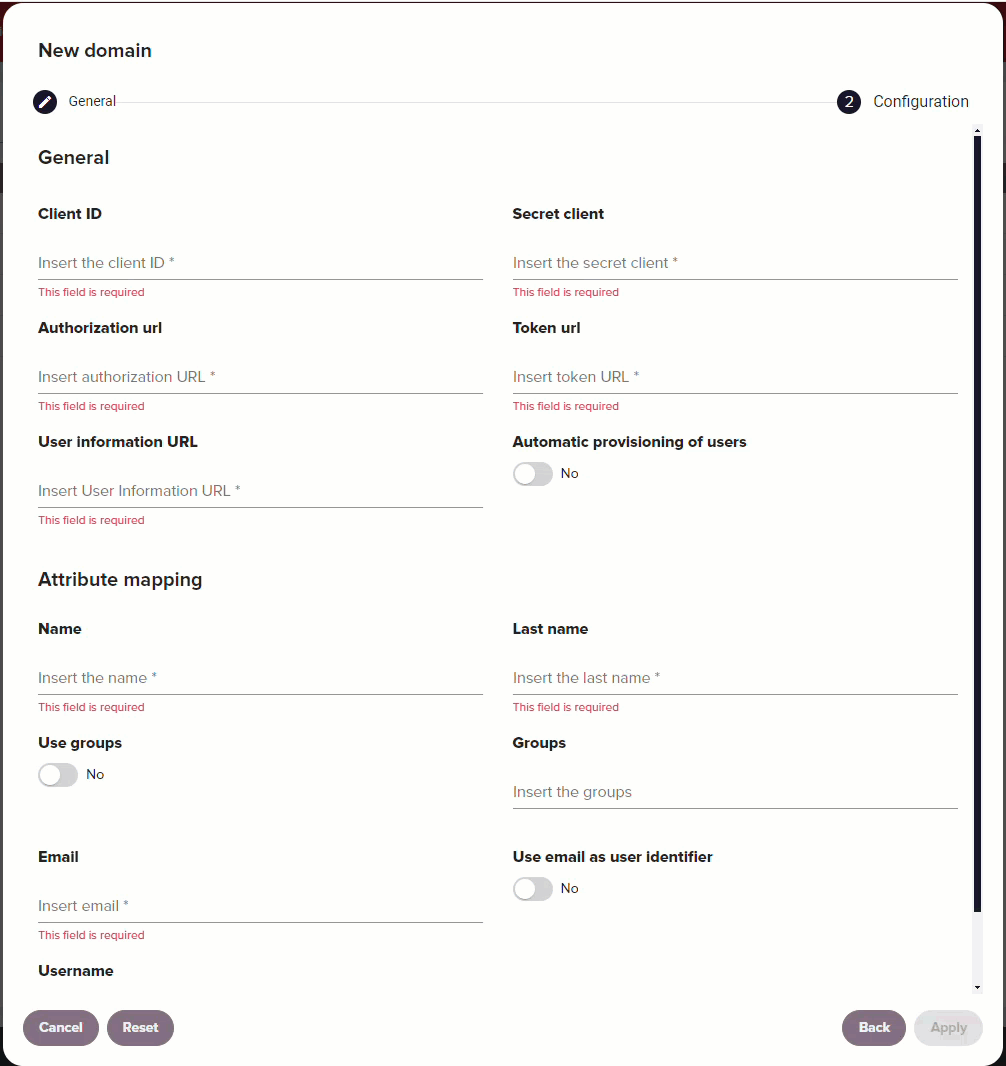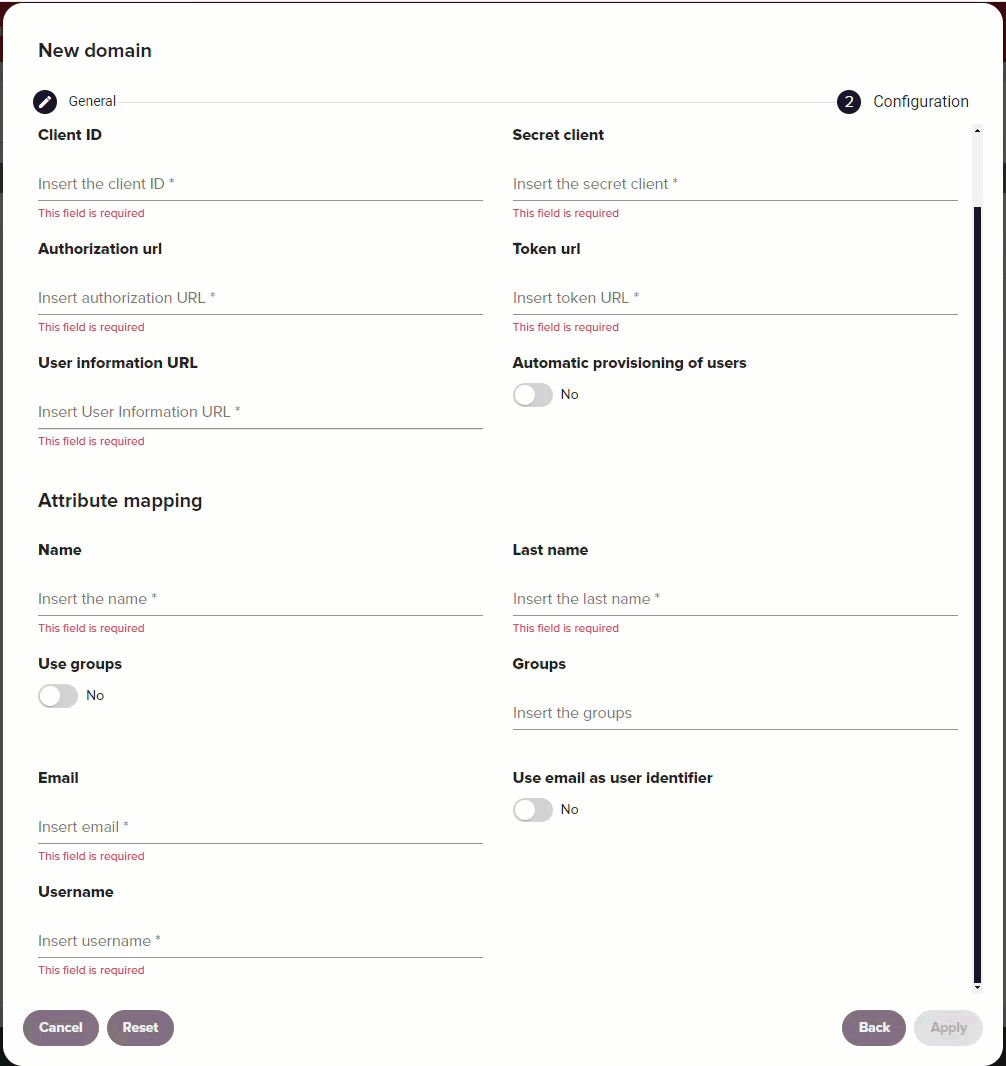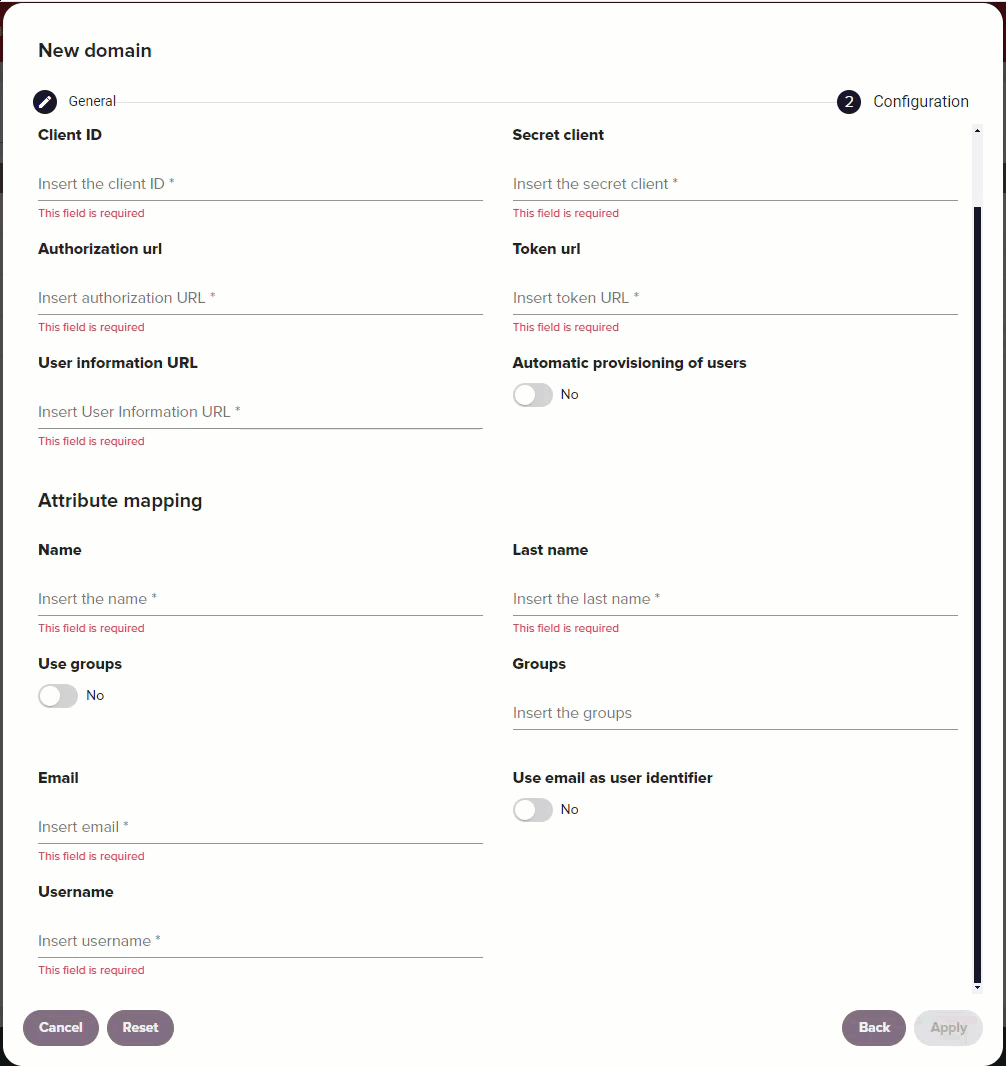
| Option | Description |
|---|---|
| General | |
| Client ID | App identifier. Provided by your IdP. |
| Secret client | App authentication key. Provided by your IdP. |
| Authorization URL | Endpoint to login and consent. Provided by your IdP. |
| Token URL | Endpoint to exchange for access token. Provided by your IdP. |
| User information URL | Endpoint to fetch user data. Provided by your IdP. |
| Automatic provisioning of users | If enabled, this setting imports a user's email, name, and group membership in Redtrust the first time the user authenticates against the IdP. If this setting isn't enabled, you need to manually populate these data fields for users. |
| Attribute mapping | |
| Name | The value you have configured for the name attribute from your IdP. |
| Last name | The value you have configured for the last name attribute from your IdP. |
| Use groups | Enable to have Redtrust use a user's group membership in the claim. |
| Groups | The value you have configured for the groups attribute from your IdP. |
The value you have configured for the email attribute from your IdP. | |
| Use email as user identifier | Enable this option if your organization uses the email attribute as the identifier for users instead of the username. Note: This option needs to be configured at the time of domain creation. It isn't possible to edit this property once a domain has been created. |
| Username | The value you have configured for the username attribute from your IdP. This option is only available if you don't enable Use email as user identifier. |
SAML 2.0
See UI screenshot
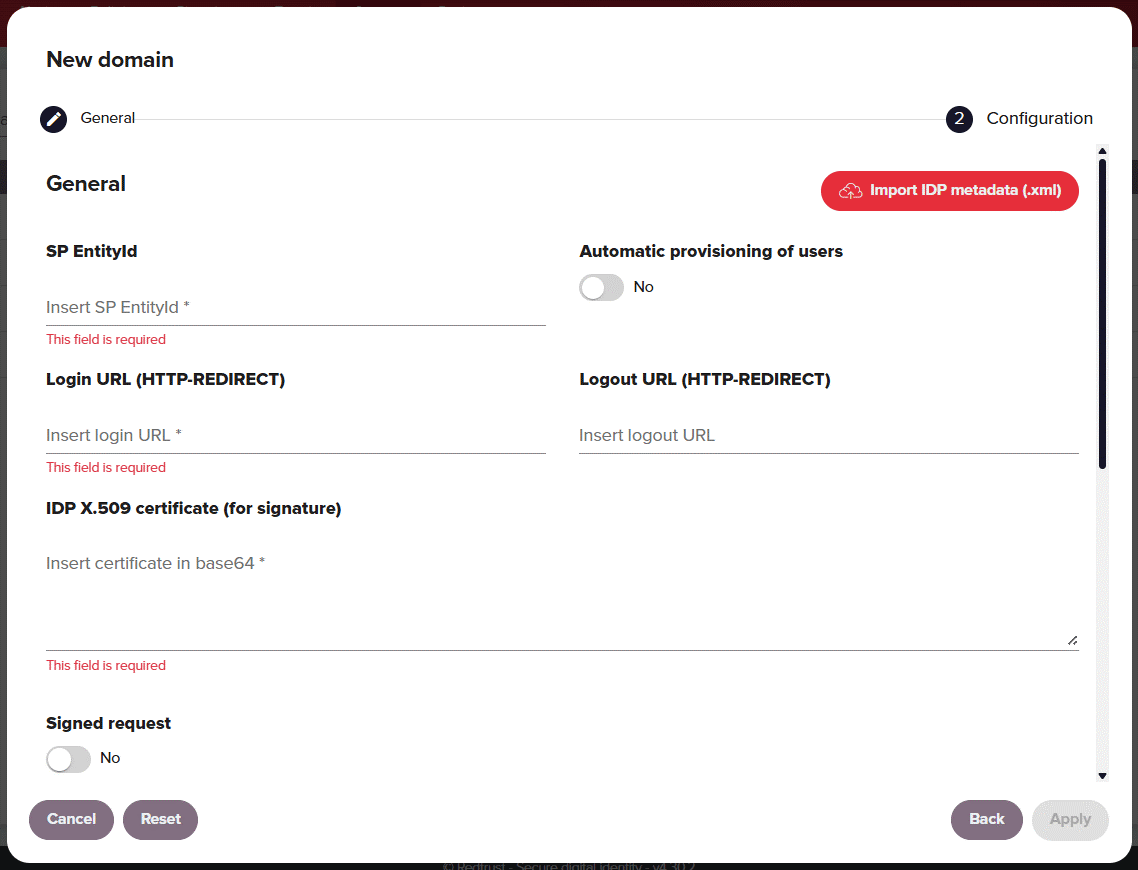
| Option | Description |
|---|---|
| General | |
| SP EntityID | This value should be https://REDTRUST_DEPLOYMENT_URL/ALIAS_OF_YOUR_DOMAIN. For example, if the alias of your SAML domain is companyname.com this would be https://redtrustdeployment.com/companyname.com. |
| Automatic provisioning of users | If enabled, this setting imports a user's email, name, and group membership in Redtrust the first time the user authenticates against the IdP. If this setting isn't enabled, you need to manually populate these data fields for users. |
| Login URL (HTTP-redirect) | Redirects users to the IdP for login. Provided by your IdP. |
| Logout URL (HTTP-redirect) | Redirects users to the IdP for logout. Provided by your IdP. |
| IDP X.509 certificate (for signature) | Verifies the IdP's digital signatures. Provided by your IdP. |
| Signed request | Enable this option to sign SAML authentication requests. You'll need to specify a Certificate source and define a validity period in Months to expiration. For more information see SAML request tutorial. |
| Attribute mapping | |
The value you have configured for the email attribute in the SAML assertion. | |
| Case sensitive NameID | When enabled this setting treats the NameID field as case sensitive. Enabled by default. |
| Name | The value you have configured for the name attribute in the SAML assertion. |
| Surname | The value you have configured for the surname attribute in the SAML assertion. |
| Use email as user identifier | Enable this option if your organization uses the email attribute as the identifier for users instead of name or surnames. Note: this option needs to be configured at the time of domain creation. It's not possible to edit this property once a domain has been created. Most use cases will want to enable this setting. |
| ACS by index | Disabled by default. This property specifies how to indicate to the IdP (through the SAML authentication request) the URL that will consume the SAML assertion generated by the IdP. If disabled, AssertionConsumerServiceURL will be added to the authentication request. If enabled, AssertionConsumerServiceIndex will be added in the request. In addition, you must configure the IdP so that the index 0 corresponds to the URL https://REDTRUST_DEPLOYMENT_URL/Auth/SamlConsumer. |
| Groups | Groups to which the user is assigned. |
You may see the error “User found, but doesn't belong to any roles” when attempting to log in to Redtrust after authenticating with the IdP. This is because every user accessing the admin console must be assigned a role and the authenticating user hasn't yet been assigned one by the Redtrust administrator. You can solve this by either having the system admin log in to Redtrust and assign this new user to a role or by using SAML groups to assign an entire group of users to a particular role. This allows those group members to automatically log in.
IdP URL configuration
Users can also be directed to the IdP login page, skipping the Redtrust login page by navigating to a URL with the below configuration. After authenticating, the user is sent back to the Redtrust admin console.
https://REDTRUST_URL/login?domain=DOMAIN_ALIAS
User configuration options
| Option | Description |
|---|---|
| Username | Username
|
| Status | Defaults to active. A user with an inactive status won't be able to login. |
| Name | Name of the user. |
| The email address for the user. | |
| Password | User password. |
| User must change password on next logon | Defines whether the user is prompted to change the password the next time they log on. |
Once the user is created, it appears in the Users tab after clicking a domain's row.
Selecting the user will bring up additional properties about the user.
| Additional User Properties | Description |
|---|---|
| Last certificate usage | The last date and time this user signed with a Redtrust certificate. |
| Locked | This option is enabled when a user is locked out due to the local user domain password policy. The Redtrust administrator can toggle it to unlock the account. |