Events
Overview
The Events section of the Redtrust admin console provides authorized users with a detailed view of application and client activities. Anytime a remote user or agent attempts to access a certificate or perform an action in the admin console, the activity is logged and displayed in the admin console, where it can be viewed or exported. The Redtrust administrator can monitor event logs, which record certificate usage, and system logs, which capture admin console activity.
Types of events
Events fall into two types:
- Session events: These events occur as a result of a user's login attempt. These include:
- The user iDUser has started a new session: The user has successfully logged in to the system through the agent.
- Accepted connection from application: The user accessed an application configured in a user-defined policy, and the connection was accepted.
- Rejected connection from application: The user attempted to access an application configured in a user-defined policy, but the connection was rejected.
- The user iDUser ended his session: The user has finished his session in the system through the agent.
The Description column in the event list provides details about each session event.
- Certificate events: These events occur as a result of the use of a certificate. These include:
- Authorized use of certificate
- Permission denied
- Wrong PIN entered
Events log
The Events tab in the Events section of the admin console logs certificate usage activities performed by clients.
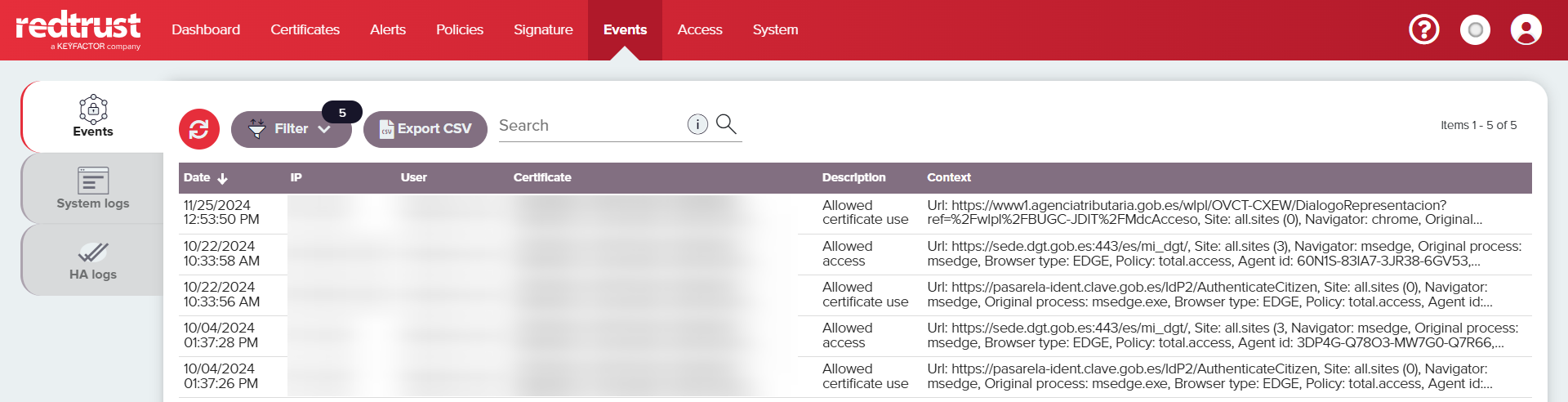
Selecting an individual event displays additional information about that event.
| Event log | Description |
|---|---|
| Date | Date of the event. |
| IP | The client's IP address. |
| User | The user logged into the client agent during the certificate's usage. |
| Description | Whether the policy allowed or denied permissions. |
| Certificate | The certificate used during the event. |
| Context |
|
Due to Apple restrictions, MacOS does not allow access to application or website information in use, so you can neither limit access by URL or process, nor audit URLs or processes where the certificate has been used.
System logs
The System logs tab in the Events section of the admin console records user activity within the console. These logs are visible only to users with the appropriate permissions.
| System log | Description |
|---|---|
| Date | Date and time when the event occurred. |
| IP | IP address of the client initiating the request. |
| User | Username of the person logged into the admin console. |
| Section | Area of the admin console where the action took place. |
| Information | Details of the event. For example, successful login or logout attempts, edits to policies or certificates, etc. Actions performed via the API are also recorded here. |
If some data was edited, you can see the changes in the last section of the event view window.