DSS API Examples
Below you can see some examples of SOAP calls to the service. All the calls in the examples are SOAP 1.2 and have a user/password authentication.
GetAccessibleCertificates: Retrieves the list of certificates to which the authenticated user has access. The following example returns the certificates to which the username@domain user has permissions in the signing service. These certificates are those personal to the user and those to which he has access by policy.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:evolium:redtrust:dss:ws">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PSSWORD]</wsse:Password>
<wsu:Created>2024-11-15T11:28:30.080Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/GetAccessibleCertificates</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<urn:GetAccessibleCertificates/>
</soap:Body>
</soap:Envelope>
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/GetAccessibleCertificatesResponse</a:Action>
</s:Header>
<s:Body>
<GetAccessibleCertificatesResponse xmlns="urn:evolium:redtrust:dss:ws">
<Result xmlns:b="http://schemas.datacontract.org/2004/07/RTDSSService" xmlns:i="http://www.w3.org/2001/XMLSchema-instance">
<b:ResultStatus>SUCCESS</b:ResultStatus>
<b:ResultMessage>Operation finalized successfully</b:ResultMessage>
<b:ResultData i:type="b:ArrayOfCertificate">
<b:Certificate>
<b:X509Data>...</b:X509Data>
<b:alias>EIDAS CERTIFICADO PRUEBAS - 99999999R</b:alias>
<b:certificateHandler>6017</b:certificateHandler>
<b:expiration>2024-11-05T14:04:20</b:expiration>
<b:issuer>Ceres</b:issuer>
<b:needPin>false</b:needPin>
<b:needReason>false</b:needReason>
<b:subject>EIDAS CERTIFICADO PRUEBAS - 99999999R</b:subject>
<b:thumbprint>06F13CCD80E271D5355B3BEA322B8CBCE25B35F6</b:thumbprint>
<b:type>PRIVATE</b:type>
</b:Certificate>
</b:ResultData>
<b:TotalItems>1</b:TotalItems>
</Result>
</GetAccessibleCertificatesResponse>
</s:Body>
</s:Envelope>
In the response you get a Result object, with a ResultStatus in success status indicating that no error has occurred. You also get a ResultMessage with a descriptive message and a ResultData object which is a list of Certificate objects.
Each Certificate object contains the information necessary for its use. For example the following:
| Parameters | Description |
|---|---|
needPin | To know if you need a PIN to use it. |
thumbprint | Identifier used in SignHash, SignRequest expiration to know if it's expired or not. |
alias | Name given to the certificate from the Redtrust configuration. |
issue or subject | Information extracted directly from the certificate for those fields or the thumbprint itself. |
X509Data | Public part of the certificate. The content of this attribute is Base64 encoded so that it can be included in the response. |
Hash signature
Generates a PKCS#1 signature from a hash. The certificates allowed for the signature are those obtained in the GetAccessibleCertificates method. Both the id and the thumbprint of the chosen certificate can be specified to make the call.
Requirements
- The hash signature must be enabled on the server.
- A certificate with the request identifier must exist.
- A username@domain user must exist.
- There must be a usage policy that allows the user to use the certificate for signing documents or it must be the user's personal certificate.
The hash signature capability isn't enabled by default with the signature service license and must be requested to the support team.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:evolium:redtrust:dss:ws">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="UsernameToken-5F01A1638C9F9A33A1173167092288930">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PSSWORD]</wsse:Password>
<wsu:Created>2024-11-15T11:42:02.889Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignHash</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<urn:SignHash>
<!--Optional:-->
<urn:toSignHashB64>ybWpO/j3yCfUhzWEWqdHcDgyQ8l5CWwea6Hj+GpI2CA=</urn:toSignHashB64>
<!--Optional:-->
<urn:thumbprint>06F13CCD80E271D5355B3BEA322B8CBCE25B35F6</urn:thumbprint>
<!--Optional:-->
<!--<urn:certificatePin>?</urn:certificatePin>-->
<!--Optional:-->
<urn:algorithm>RSA_SHA256</urn:algorithm>
</urn:SignHash>
</soap:Body>
</soap:Envelope>
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignHashResponse</a:Action>
</s:Header>
<s:Body>
<SignHashResponse xmlns="urn:evolium:redtrust:dss:ws">
<Result xmlns:b="http://schemas.datacontract.org/2004/07/RTDSSService" xmlns:i="http://www.w3.org/2001/XMLSchema-instance">
<b:ResultStatus>SUCCESS</b:ResultStatus>
<b:ResultMessage>Operation finalized successfully</b:ResultMessage>
<b:ResultData i:type="c:string" xmlns:c="http://www.w3.org/2001/XMLSchema">JCtCs3wdvCl1Ql0tstzkMczNmNxcnaLNospXPB/miOi++fbG+jP6dTRvBwhJ4triE8TXxXMs5aVyCkl0oj+WumoO2zRGZSSk1mcbjrYuKP8m+gj5yp0bOGGPbvAIaphhqV87oU+2kcyCtNt32E0QQGRGW6kr+ADPctOFOD5loV84hRUqAw8AJQX20XjlKtzkhaDGBQFMGVUODAId/ywpxCYIQOetRXWcLfCNHQE/C4+jaNwamvPTGlVhn0Vr6xWAoN0/BKBk5eDVOynX7J2zl7TErkVrZ4WA2cIbxxuq2vj1MUMV89dDB54E4cc7UduYKzMIj0iEJ+19NL47NM96iQ==</b:ResultData>
</Result>
</SignHashResponse>
</s:Body>
</s:Envelope>
The input parameters of the method are:
| Parameters | Description |
|---|---|
toSignHash | Base64 encoded binary hash. |
thumbprint | Fingerprint of the certificate. |
certificatePin | Certificate PIN (Optional). |
algorithm | Hashing algorithm, accepted values are RSA_SHA1, RSA_SHA256, RSA_SHA512, ECDSA_SHA256, ECDSA_SHA384, ECDSA_SHA512. |
In response you get a Result object with the following fields:
| Field | Description |
|---|---|
| ResultStatus | Result code, SUCCESS if the signature was successful. |
| ResultMessage | Message describing the result of the operation. |
| ResultData | Contains the result of the operation if the signature was successful (Optional). |
See Appendix 3 Result Response Codes of this document for possible error codes you may get in the response.
DSS Signature
Description of the fields of a SignRequest.
<soap:Header>
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>developer@local.users</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">1234</wsse:Password>
<wsu:Created>2024-11-15T11:28:30.080Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://127.0.0.1:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
| Field | Description |
|---|---|
| Fields in the header | |
| username@domain | Corresponds to the Redtrust user who is going to make the signature request. |
| password | User's password. |
| Body fields | |
| signature_pdf | Corresponds to the signature profile previously created in Redtrust and that defines how the signature should be made. |
| en-US | Language selected for reply messages. If not specified, the Redtrust configured language will be applied by default. |
| 403C7691336CDB7E04F9F272A602A4B42CBE298D | Identifier of the certificate that will be used to sign the document and corresponds to the field Fingerprint (thumbprint) of the same. The certificate must be registered in the platform. It can only be used if the user has access to the certificate through a Redtrust policy that allows its use in the signature service or if it's a personal certificate. |
| 1234 | PIN of the certificate, only if necessary. |
| urn:oasis:names:tc:dss:1.0:profiles:PAdES:forms:LTV | The form you want the signature to take. It must be a valid value for the profile and in case it's not specified it must be forced in the profile. |
| JVBERi0xLjQNJe...Nw0lJUVPRg0= | Document to be signed encoded in Base64. |
XAdES
XAdES (XML Advanced Electronic Signature) is a set of extensions to XmlDSig that make it suitable for electronic signature, according to the European Union directive 1999/93/EC. One of the strengths of XAdES is that documents electronically signed using this system can remain valid for long periods of time.
Examples of the use of Redtrust's DSS service for signing XML documents using XAdES are shown below.
XAdES BES Enveloped Signature
This example describes how to make a call to the service to generate an XAdES signature in BES level and enveloped mode. The BES level is the most basic of the advanced signature, as described in the section Supported levels. The enveloped mode embeds the signature within the original document, as described in the Supported modes section.
Requirements
- There must be a signature profile in Redtrust defined for XAdES. The name must be XAdES, with the BES level selected (forced or not), enveloped mode selected (forced or not), the signing algorithm will depend on the certificate, typically RSA, and the digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="XAdES-BES-Enveloped-RSA-SHA256" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
<SignaturePlacement WhichDocument="ID-document-1"/>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64XML>PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz4KPG1lc3NhZ2U+CiAgICA8dGV4
dD5IZWxsbyBXb3JsZDwvdGV4dD4KPC9tZXNzYWdlPgo=</Base64XML>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
In the request you can see the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certified thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES, the SignaturePlacement tag that specifies the enveloped mode and the XML document to be signed encoded in Base64 within the Base64XML tag.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="XAdES-BES-Enveloped-RSA-SHA256" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<OptionalOutputs>
<dss:DocumentWithSignature xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:rt="urn:evolium:redtrust:dss:1.0:core:schema" xmlns:xades="http://uri.etsi.org/01903/v1.3.2#">
<dss:Document ID="ID-document-1">
<dss:Base64XML>...</dss:Base64XML>
</dss:Document>
</dss:DocumentWithSignature>
</OptionalOutputs>
<SignatureObject>
<SignaturePtr WhichDocument="ID-document-1"/>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag, a SignaturePtr tag which is a reference to where the document is located within the response and finally the Base64XML tag which contains the document with the embedded signature encoded in Base64.
XAdES BES enveloping signature
This example describes how to make a call to the service to generate an XAdES signature at BES level and enveloping mode. The BES level is the most basic of the advanced signature, as described in the section Supported levels. The enveloping mode embeds the original document within the signature, as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for XAdES. The name must be XAdES, with the BES level selected (forced or not), enveloping mode selected (forced or not), the signing algorithm will depend on the certificate, typically RSA, and the digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or it must be a personal certificate of the user.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="XAdES enveloping" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
<IncludeObject WhichDocument="ID-document-1"/>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<InlineXML>
<Document>
<Chapter>Text</Chapter>
</Document>
</InlineXML>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header, the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES, the SignaturePlacement tag specifies the enveloping mode and the XML document to sign directly embedded inside the InlineXML tag.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="XAdES enveloping" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3275">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag and a Base64Signature tag containing the signature with the embedded document encoded in Base64.
XAdES BES detached signature
This example describes how to make a call to the service to generate an XAdES signature at BES level and detached mode. The BES level is the most basic of the advanced signature, as described in the section Supported levels. The detached mode generated a signature detached from the original document, as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for XAdES. The name must be XAdES, with the BES level selected (forced or not), detached mode selected (forced or not), the signing algorithm will depend on the certificate, typically RSA, and the digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or it must be a personal certificate of the user.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="XAdES-BES-Detached" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<EscapedXML><Document><Chapter>Text</Chapter></Document></EscapedXML>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header, the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign with, the SignatureForm tag that specifies that the level is BES and the XML document to sign escaped embedded inside the EscapedXML tag. The absence of the SignaturePlacement tag specifies that the mode is forced in the signature profile or, if not forced, the mode is detached.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="XAdES-BES-Detached" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3275">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag and a Base64Signature tag containing the Base64 encoded signature.
XAdES T enveloped signature
This example describes how to make a call to the service to generate an XAdES signature in T level and enveloped mode. The T-level adds a timestamp to the signature, as described in the section Supported levels. The enveloped mode embeds the signature within the original document, as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for XAdES. The name must be XAdES, with T-level selected (forced or not), enveloped mode selected (forced or not), signing algorithm will depend on the certificate, typically RSA, and SHA256 digest algorithm, and at least one valid TSP selected as primary or secondary.
- There must be a certificate with the request identifier, PIN protected.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or use a personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="XAdES-T-Forced-Enveloped-Forced-RSA-SHA256" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<AdditionalKeyInfo>
<KeyInfo Id="Pin" xmlns="http://www.w3.org/2000/09/xmldsig#">1234</KeyInfo>
</AdditionalKeyInfo>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:ES-T</SignatureForm>
<SignaturePlacement WhichDocument="ID-document-1"/>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64XML>PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz4KPG1lc3NhZ2U+CiAgICA8dGV4dD5IZWxsbyBXb3JsZDwvdGV4dD4KPC9tZXNzYWdlPgo=</Base64XML>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header, the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign with and in the AdditionalKeyInfo tag the certificate PIN information, the SignatureForm tag that specifies that the level will be BES, the SignaturePlacement tag that specifies the enveloped mode and the XML document to sign encoded in Base64 inside the Base64XML tag.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="XAdES-T-Forced-Enveloped-Forced-RSA-SHA256" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<OptionalOutputs>
<dss:DocumentWithSignature xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:rt="urn:evolium:redtrust:dss:1.0:core:schema" xmlns:xades="http://uri.etsi.org/01903/v1.3.2#">
<dss:Document ID="ID-document-1">
<dss:Base64XML>...</dss:Base64XML>
</dss:Document>
</dss:DocumentWithSignature>
</OptionalOutputs>
<SignatureObject>
<SignaturePtr WhichDocument="ID-document-1"/>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the general status of the request in the ResultMajor tag, a SignaturePtr tag which is a reference to where the document is located within the response and finally the Base64XML tag which contains the document with the embedded signature encoded in Base64. The signature will contain a time stamp, which protects the signature against repudiation.
Signature FacturaE 3.0 (XAdES EPES enveloped)
This example describes how to make a call to the service to generate an XAdES signature at EPES level (with a signature policy), with enveloped mode. The EPES level is the same as the BES level only that a signature policy has been defined, as described in the section Supported levels. The enveloped mode embeds the signature within the original document, as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for XAdES. The name must be
FacturaE_3.0, with BES or EPES level selected forced, enveloped mode selected forced, signature algorithm will depend on the certificate, typically RSA, and digest algorithm SHA256. In Policies you must include the following information:- OID: http://www.facturae.gob.es/ signature policy facturae format/signature-policy facturae format v3_0.pdf
- Hash:
HQvPemjDslVpcNmaJPpbHzhdZ50== Hash algorithm:HQvPemjDslVpcNmaJPpbHzhdZ50= - Hash algorithm:
sha1.
- A certificate with the request identifier must exist.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate to sign documents or to use the user's personal certificate.
The document to be signed must be a valid XML according to the facturae 3.0 schema defined in the URL http://www.facturae.gob.es/formato/Versiones%20anteriores/B)%20Versi%C3%B3n%203.0/Facturae30.xml.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="XAdES-Facturae_3.0-EPES_Forced-Enveloped-RSA-SHA256" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:EPES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64XML>...</Base64XML>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign and the XML document to sign encoded in Base64 inside the Base64XML tag. As both the mode and the level are forced in profile, there is no need to specify anything in the request.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="XAdES-Facturae_3.0-EPES_Forced-Enveloped-RSA-SHA256" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3275">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the general status of the request in the ResultMajor tag, a SignaturePtr tag which is a reference to where the document is located within the response and finally the Base64XML tag which contains the document with the embedded signature encoded in Base64. By including the signature policy in the profile, the signature will contain that information and will be valid as an e-invoice 3.0, provided that the input document is valid according to the schema. Redtrust doesn't validate the XML format, it's your responsibility to validate the format, if necessary, before sending the request to the service.
Signature FacturaE 3.2 (XAdES EPES enveloped)
This example describes how to make a call to the service to generate an XAdES signature at EPES level (with a signature policy), with enveloped mode. The EPES level is the same as the BES level only that a signature policy has been defined, as described in the section Supported levels. The enveloped mode embeds the signature within the original document, as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for XAdES. The name must be
FacturaE_3.1_3.2, with BES or EPES level selected (forced or not), enveloped mode selected (forced or not), signature algorithm will depend on the certificate, typically RSA, and digest algorithm SHA256. In Policies you must include the following information:- OID: https://www.facturae.gob.es/formato/Polticasfirma/A)%20Versi%C3%B3n%203.1/Politica_Firma_formato_facturae_v3_1.pdf
- Hash:
Ohixl6upD6av8N7pEvDABhEL6hM= - Hash algorithm:
sha1.
- A certificate with the request identifier must exist.
- A username@domain user must exist.
- There must be a usage policy that allows the user to use the certificate for signing documents or use a personal certificate.
The document to be signed must be a valid XML according to the facturae 3.0 schema defined in the URL http://www.facturae.gob.es/formato/Versiones/Facturaev3_2.xml.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="XAdES-Facturae_3.1_3.2-EPES-Forced-Enveloped-Forced-RSA-SHA2" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignaturePlacement WhichDocument="ID-document-1"/>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64XML>...</Base64XML>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign and the XML document to sign encoded in Base64 inside the Base64XML tag. As both the mode and the level are forced in profile, there is no need to specify anything in the request.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="XAdES-Facturae_3.1_3.2-EPES-Forced-Enveloped-Forced-RSA-SHA2" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<OptionalOutputs>
<dss:DocumentWithSignature xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:rt="urn:evolium:redtrust:dss:1.0:core:schema" xmlns:xades="http://uri.etsi.org/01903/v1.3.2#">
<dss:Document ID="ID-document-1">
<dss:Base64XML>...</dss:Base64XML>
</dss:Document>
</dss:DocumentWithSignature>
</OptionalOutputs>
<SignatureObject>
<SignaturePtr WhichDocument="ID-document-1"/>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the general status of the request in the ResultMajor tag, a SignaturePtr tag which is a reference to where the document is located within the response and finally the Base64XML tag which contains the document with the embedded signature encoded in Base64. By including the signature policy in the profile, the signature will contain that information and will be valid as an electronic invoice 3.2, as long as the input document is valid according to the schema. Redtrust doesn't validate XML formatting, it's your responsibility to validate the formatting before submitting the request to the service.
CAdES (CMS Advanced Electronic Signature)
CAdES (CMS Advanced Electronic Signature) is a set of CMS extensions that make it suitable for electronic signature, according to the European Union directive 1999/93/EC. Like XAdES, one of the strengths of CAdES is that documents electronically signed using CAdES can remain valid for long periods of time.
Below are a few examples of using Redtrust's DSS service to sign documents using CAdES.
CAdES BES enveloping signature
This example describes how to make a call to the service to generate a CAdES signature in BES level and enveloping mode. The BES level is the most basic of the advanced signature, as described in section [Supported levels](index.md#supported-levels). The enveloping mode embeds the original document within the signature, as described in the section Supported modes.
Requirements.
- There must be a signature profile in Redtrust defined for CAdES. The name must be CAdES, with the BES level selected (forced or not), enveloping mode selected (forced or not), signing algorithm will depend on the certificate, typically RSA, and digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="CAdES-BES-Enveloping" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<IncludeEContent/>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="text/plain">RmljaGVybyBkZSBwcnVlYmEgYSBmaXJtYXI=</Base64Data>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES, the IncludeEContent tag specifies that the mode has to be enveloping and the XML document to sign encoded in Base64 inside the Base64Data tag.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="CAdES-BES-Enveloping" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3369">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag, a Base64Signature tag containing the signature with the embedded document encoded in Base64.
CAdES BES Detached Signature
This example describes how to make a call to the service to generate a CAdES signature in BES level and detached mode. The BES level is the most basic of the advanced signature, as described in the section Supported levels. The detached mode generates a signature separate from the document, as described in the section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for CAdES. The name must be CAdES, with BES level selected (forced or not), detached mode selected (forced or not), signing algorithm will depend on the certificate, typically RSA, and digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="CAdES-BES-Detached" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<dss:Language xmlns:dss="urn:oasis:names:tc:dss:1.0:core:schema">en-US</dss:Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="text/plain">RmljaGVybyBkZSBwcnVlYmEgYSBmaXJtYXI=</Base64Data>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certificate thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES and the XML document to sign encoded in Base64 inside the Base64Data tag. The absence of the IncludeEContent tag specifies that the forced mode is used in the profile or if the detached mode isn't forced.
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="CAdES-BES-Detached" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3369">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag, a Base64Signature tag containing the Base64 encoded signature.
PAdES
PAdES (PDF Advanced Electronic Signature) is a set of extensions to PDF and ISO 32000-1 that make it suitable for electronic signature, according to the European Union directive 1999/93/EC.
A few examples of using Redtrust's DSS service to sign documents using PAdES will be shown below.
BES PDF Signature
This example describes how to make a call to the service to generate a PAdES signature at the BES level. The BES level is the most basic of the advanced signature, as described in the section Supported levels. PAdES only supports enveloped mode as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for PAdES. The name must be PAdES, with the BES level selected (forced or not), enveloped mode. The signature algorithm will depend on the certificate, normally RSA, and digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="PAdES_BES" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<Language>en-US</Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="application/pdf">...</Base64Data>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certified thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES and the PDF document to sign encoded in Base64 inside the Base64Data tag (the MimeType=“application/pdf” attribute specifies that the content of the tag corresponds to a PDF).
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="PAdES_BES" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3369">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag, a Base64Signature tag containing the PDF file with the signature encoded in Base64.
Visible BES PDF Signature
This example describes how to make a call to the service to generate a PAdES signature at BES level and with visual representation of the signature. The BES level is the most basic of the advanced signature, as described in the section Supported levels. PAdES only supports enveloped mode as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for PAdES. The name must be PAdES, with the BES level selected (forced or not), enveloped mode, signature algorithm will depend on the certificate, typically RSA, and digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="PAdES_BES" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<q1:VisibleSignatureConfiguration xmlns:q1="urn:oasis:names:tc:dssx:1.0:profiles:VisibleSignatures:schema#">
<q1:VisibleSignaturePolicy>GeneralPolicy</q1:VisibleSignaturePolicy>
<q1:VisibleSignaturePosition d4p1:type="q1:PixelVisibleSignaturePositionType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:PageNumber>1</q1:PageNumber>
<q1:x>30</q1:x>
<q1:y>30</q1:y>
<q1:Width>200</q1:Width>
<q1:Height>60</q1:Height>
</q1:VisibleSignaturePosition>
<q1:VisibleSignatureItemsConfiguration>
<q1:VisibleSignatureItem>
<q1:ItemName>CustomText</q1:ItemName>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureReason</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Razón de firma</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureProductionPlace</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Barcelona</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerContactInfo</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Usuario de Redtrust (usuario.Redtrust@evolium.com)</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
</q1:VisibleSignatureItemsConfiguration>
</q1:VisibleSignatureConfiguration>
<Language>en-US</Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="application/pdf">...</Base64Data>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
The request shows the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certified thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES and the PDF document to sign encoded in Base64 inside the Base64Data tag (the MimeType=“application/pdf” attribute specifies that the content of the tag corresponds to a PDF).
The visual representation part of the signature is located inside the VisibleSignatureConfiguration tag and contains:
| Tag | Description |
|---|---|
VisibleSignaturePolicy | Contains the text GeneralPolicy, which is the only visual representation policy accepted by Redtrust. |
VisibleSignaturePosition | Specifies the location (counting from the lower left corner) and size in pixels of the display. |
VisibleSignatureItemsConfiguration | Contains a sequence of elements that indicate how the visual signature will look like, in this case a reason (SignatureReason), a signing location (SignatureProductionPlace), signer contact information (SignerContactInfo) and a CustomText item that indicates that the visual representation of the signature will contain a descriptive text of the certificate, namely the content of SubjectName. |
The signature would look as shown in the following representation:

Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="PAdES_BES" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3369">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag, a Base64Signature tag containing the PDF file with the signature encoded in Base64.
Visible PDF BES signature with signature image
This example describes how to make a call to the service to generate a PAdES signature at BES level and with visual representation of the signature with image. The BES level is the most basic of the advanced signature, as described in the section Supported levels. PAdES only supports enveloped mode as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for PAdES. The name must be PAdES, with the BES level selected (forced or not), enveloped mode, signature algorithm will depend on the certificate, typically RSA, and digest algorithm SHA256.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="PAdES_BES" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<q1:VisibleSignatureConfiguration xmlns:q1="urn:oasis:names:tc:dssx:1.0:profiles:VisibleSignatures:schema#">
<q1:VisibleSignaturePolicy>GeneralPolicy</q1:VisibleSignaturePolicy>
<q1:VisibleSignaturePosition d4p1:type="q1:PixelVisibleSignaturePositionType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:PageNumber>1</q1:PageNumber>
<q1:x>30</q1:x>
<q1:y>20</q1:y>
<q1:Width>200</q1:Width>
<q1:Height>75</q1:Height>
</q1:VisibleSignaturePosition>
<q1:VisibleSignatureItemsConfiguration>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureReason</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Razón de firma</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureProductionPlace</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Barcelona</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>CustomText</q1:ItemName>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerContactInfo</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Usuario Demo (user@demo.com)</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerImage</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueURIType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>https://upload.wikimedia.org/wikipedia/commons/thumb/a/af/Miguel_de_Cervantes_signature.svg/1280px-Miguel_de_Cervantes_signature.svg.png</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
</q1:VisibleSignatureItemsConfiguration>
</q1:VisibleSignatureConfiguration>
<Language>en-US</Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="application/pdf"><soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="PAdES_BES" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<q1:VisibleSignatureConfiguration xmlns:q1="urn:oasis:names:tc:dssx:1.0:profiles:VisibleSignatures:schema#">
<q1:VisibleSignaturePolicy>GeneralPolicy</q1:VisibleSignaturePolicy>
<q1:VisibleSignaturePosition d4p1:type="q1:PixelVisibleSignaturePositionType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:PageNumber>1</q1:PageNumber>
<q1:x>30</q1:x>
<q1:y>20</q1:y>
<q1:Width>200</q1:Width>
<q1:Height>75</q1:Height>
</q1:VisibleSignaturePosition>
<q1:VisibleSignatureItemsConfiguration>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureReason</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Razón de firma</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureProductionPlace</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Barcelona</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>CustomText</q1:ItemName>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerContactInfo</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Usuario Demo (user@demo.com)</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerImage</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueURIType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>https://upload.wikimedia.org/wikipedia/commons/thumb/a/af/Miguel_de_Cervantes_signature.svg/1280px-Miguel_de_Cervantes_signature.svg.png</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
</q1:VisibleSignatureItemsConfiguration>
</q1:VisibleSignatureConfiguration>
<Language>en-US</Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:XAdES:forms:BES</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="application/pdf">...</Base64Data>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
In the request you can see the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certified thumbprint to sign with, the SignatureForm tag that specifies that the level will be BES and the PDF document to sign encoded in Base64 inside the Base64Data tag (the MimeType=“application/pdf” attribute specifies that the content of the tag corresponds to a PDF).
The visual representation part of the signature is located inside the VisibleSignatureConfiguration tag and contains:
| Tag | Description |
|---|---|
VisibleSignaturePolicy | With the text GeneralPolicy, which is the only visual representation policy accepted by Redtrust. |
VisibleSignaturePosition | Specifies the location (counting from the lower left corner) and size in pixels of the visual representation and a VisibleSignatureItemsConfiguration tag with a sequence of items indicating how the visual signature is to be, in this case a reason is added (SignatureReason), a place where it was signed (SignatureProductionPlace), a contact information of the signer (SignerContactInfo), a CustomText item indicating that the visual representation of the signature will contain a descriptive text of the certificate and a SignerImage indicating where is the image to embed as a visual signature. |
In this case, by specifying CustomText and SignerImage the space where the signature appears will be shared between the SubjectName of the certificate and the image, as shown in the following image:
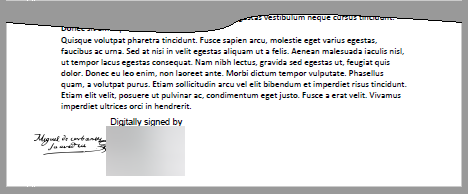
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="PAdES_BES" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3369">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
The response shows the overall status of the request in the ResultMajor tag, a Base64Signature tag containing the PDF file with the signature encoded in Base64.
LTV PDF signature
This example describes how to make a call to the service to generate a PAdES signature at LTV level. The LTV level is the long-lived signature format, allowing its validation in the future, as described in the section Supported levels. PAdES only supports enveloped mode as described in section Supported modes.
Requirements
- There must be a signature profile in Redtrust defined for PAdES. The name must be PAdES, with LTV level selected (forced or not), enveloped mode, signature algorithm will depend on the certificate, typically RSA, digest algorithm SHA256 and at least one valid TSP selected as primary or secondary.
- There must be a certificate with the request identifier.
- There must be a username@domain user.
- There must be a usage policy that allows the user to use the certificate for signing documents or to use the user's personal certificate.
Request
<soap:Envelope xmlns:soap="http://www.w3.org/2003/05/soap-envelope" xmlns:urn="urn:oasis:names:tc:dss:1.0:core:schema" xmlns:xd="http://www.w3.org/2000/09/xmldsig#">
<soap:Header xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsse:UsernameToken wsu:Id="0001">
<wsse:Username>[USERNAME]</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">[PASSWORD]</wsse:Password>
<wsu:Created>2024-11-15T12:14:44.617Z</wsu:Created>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action>urn:evolium:redtrust:dss:ws/RTDSSService/SignRequest</wsa:Action>
<wsa:To>https://[IP_REDTRUST]:8080/RTDSSService.svc/basic</wsa:To>
</soap:Header>
<soap:Body>
<SignRequest Profile="PAdES-LTV" RequestID="dss-sign-request-1" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<OptionalInputs>
<q1:VisibleSignatureConfiguration xmlns:q1="urn:oasis:names:tc:dssx:1.0:profiles:VisibleSignatures:schema#">
<q1:VisibleSignaturePolicy>GeneralPolicy</q1:VisibleSignaturePolicy>
<q1:VisibleSignaturePosition d4p1:type="q1:PixelVisibleSignaturePositionType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:PageNumber>1</q1:PageNumber>
<q1:x>30</q1:x>
<q1:y>20</q1:y>
<q1:Width>200</q1:Width>
<q1:Height>75</q1:Height>
</q1:VisibleSignaturePosition>
<q1:VisibleSignatureItemsConfiguration>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureReason</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Razón de firma</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignatureProductionPlace</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Barcelona</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>CustomText</q1:ItemName>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerContactInfo</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueStringType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<q1:ItemValue>Usuario Demo (user@demo.com)</q1:ItemValue>
</q1:ItemValue>
</q1:VisibleSignatureItem>
<q1:VisibleSignatureItem>
<q1:ItemName>SignerImage</q1:ItemName>
<q1:ItemValue d4p1:type="q1:ItemValueImageType" xmlns:d4p1="http://www.w3.org/2001/XMLSchema-instance">
<Base64Data>...</Base64Data>
</q1:ItemValue>
</q1:VisibleSignatureItem>
</q1:VisibleSignatureItemsConfiguration>
</q1:VisibleSignatureConfiguration>
<Language>en-US</Language>
<KeySelector>
<KeyInfo Id="Thumbprint" xmlns="http://www.w3.org/2000/09/xmldsig#">403C7691336CDB7E04F9F272A602A4B42CBE298D</KeyInfo>
</KeySelector>
<SignatureForm xmlns="urn:evolium:redtrust:dss:1.0:core:schema">urn:oasis:names:tc:dss:1.0:profiles:PAdES:forms:LTV</SignatureForm>
</OptionalInputs>
<InputDocuments>
<Document ID="ID-document-1">
<Base64Data MimeType="application/pdf">...</Base64Data>
</Document>
</InputDocuments>
</SignRequest>
</soap:Body>
</soap:Envelope>
In the request you can see the user authentication in the SOAP header and the signature profile selected in the Profile attribute of the SignRequest tag that refers to the profile defined in Redtrust. You can also see the KeyInfo with the certified thumbprint to sign with, the SignatureForm tag that specifies that the level is LTV and the PDF document to sign encoded in Base64 inside the Base64Data tag (the MimeType=“application/pdf” attribute specifies that the content of the tag corresponds to a PDF).
The visual representation part of the signature is located inside the VisibleSignatureConfiguration tag and contains:
| Tag | Description |
|---|---|
VisibleSignaturePolicy | With the text GeneralPolicy, which is the only visual representation policy accepted by Redtrust. |
VisibleSignaturePosition | Specifies the location (counting from the lower left corner) and size in pixels of the visual representation. |
VisibleSignatureItemsConfiguration | Includes a sequence of items indicating how the visual signature will look like, in this case a reason (SignatureReason), a place where it was signed (SignatureProductionPlace), a contact information of the signer (SignerContactInfo), a CustomText item indicating that the visual representation of the signature contains a descriptive text of the certificate and a SignerImage containing the image to embed as a visual signature encoded in Base64. |
Response
<s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://www.w3.org/2005/08/addressing">
<s:Header>
<a:Action s:mustUnderstand="1">urn:evolium:redtrust:dss:ws/RTDSSService/SignRequestResponse</a:Action>
</s:Header>
<s:Body xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema">
<SignResponse RequestID="dss-sign-request-1" Profile="PAdES-LTV" xmlns="urn:oasis:names:tc:dss:1.0:core:schema">
<Result>
<ResultMajor>urn:oasis:names:tc:dss:1.0:resultmajor:Success</ResultMajor>
</Result>
<SignatureObject>
<Base64Signature Type="urn:ietf:rfc:3369">...</Base64Signature>
</SignatureObject>
</SignResponse>
</s:Body>
</s:Envelope>
In the response you can see the overall status of the request in the ResultMajor tag, a Base64Signature tag that contains the PDF file with the signature encoded in Base64.
If you open the result file with Adobe Acrobat Reader DC you can check the signature in the signature panel.